TinyCheck
Description
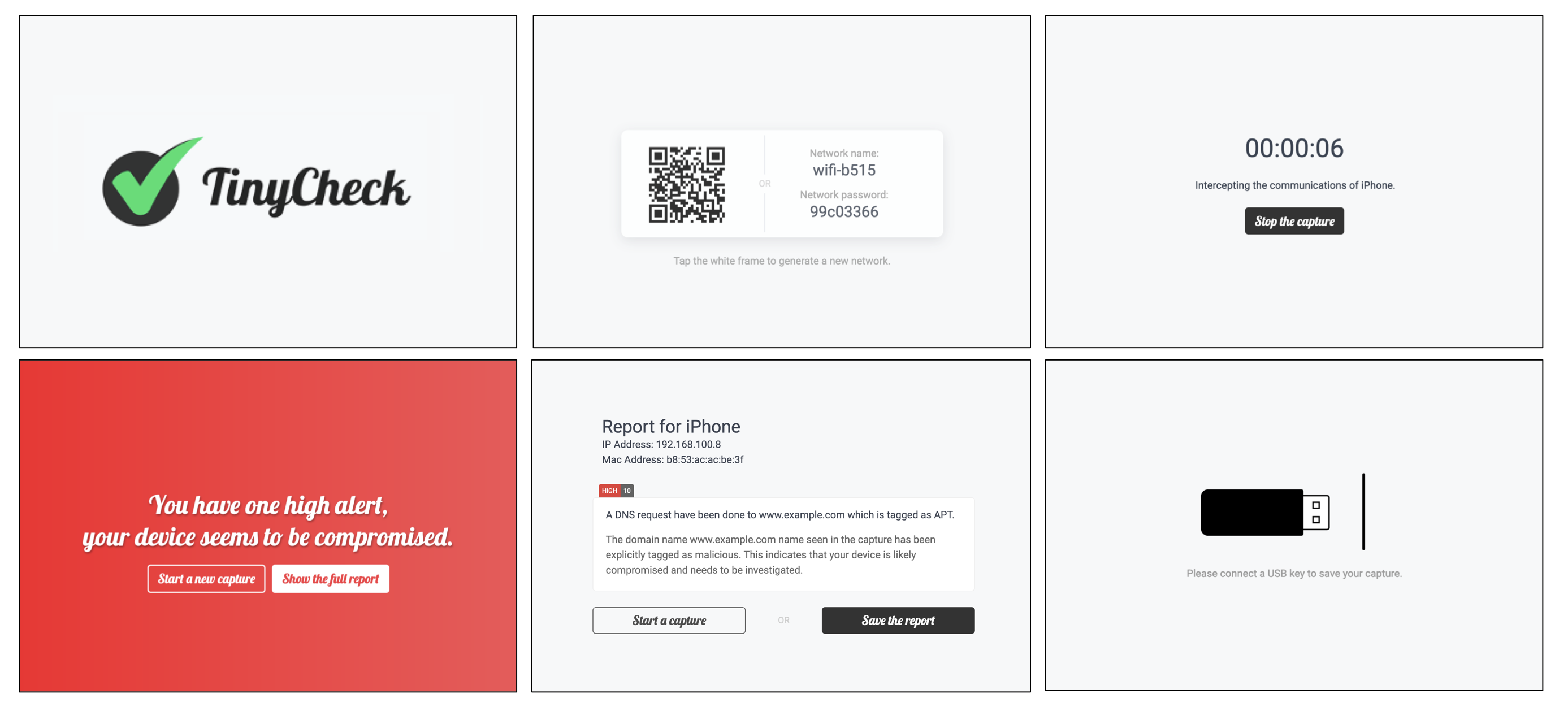
TinyCheck allows you to easily capture network communications from a smartphone or any device which can be associated to a Wi-Fi access point in order to quickly analyze them. This can be used to check if any suspect or malicious communication is outgoing from a smartphone, by using heuristics or specific Indicators of Compromise (IoCs).
The idea of TinyCheck emerged in a meeting about stalkerware with a French women's shelter. During this meeting we talked about how to easily detect stalkerware without installing very technical apps nor doing forensic analysis on the victim's smartphone. The initial concept was to develop a tiny kiosk device based on Raspberry Pi which can be used by non-tech people to test their smartphones against malicious communications issued by stalkerware or any spyware.
Of course, TinyCheck can also be used to spot any malicious communications from cybercrime to state-sponsored implants. It allows the end-user to push his own extended Indicators of Compromise via a backend in order to detect some ghosts over the wire.
If you need more documentation on how to install it, use it and the internals, don't hesitate to take a look at the TinyCheck Wiki.
If you have any question about the projet, want to contribute or just send your feedback,
don't hesitate to contact us at tinycheck[@]kaspersky[.]com.
Use cases
TinyCheck can be used in several ways by individuals and entities:
- Over a network - TinyCheck is installed on a network and can be accessed from a workstation via a browser.
- In kiosk mode - TinyCheck can be used as a kiosk to allow visitors to test their own devices.
- Fully standalone - By using a powerbank, two Wi-Fi interfaces or a 4G dongle and a small touch screen like in this video, you can tap any device anywhere.
Installation
Please check the few steps in the Wiki's Installation Page.
Meet the frontend
The frontend - which can be accessed from http://tinycheck.local is a kind of tunnel which help the user throughout the process of network capture and reporting. It allows the user to setup a Wi-Fi connection to an existing Wi-Fi network, create an ephemeral Wi-Fi network, capture the communications and show a report to the user... in less than one minute, 5 clicks and without any technical knowledge.
Meet the backend
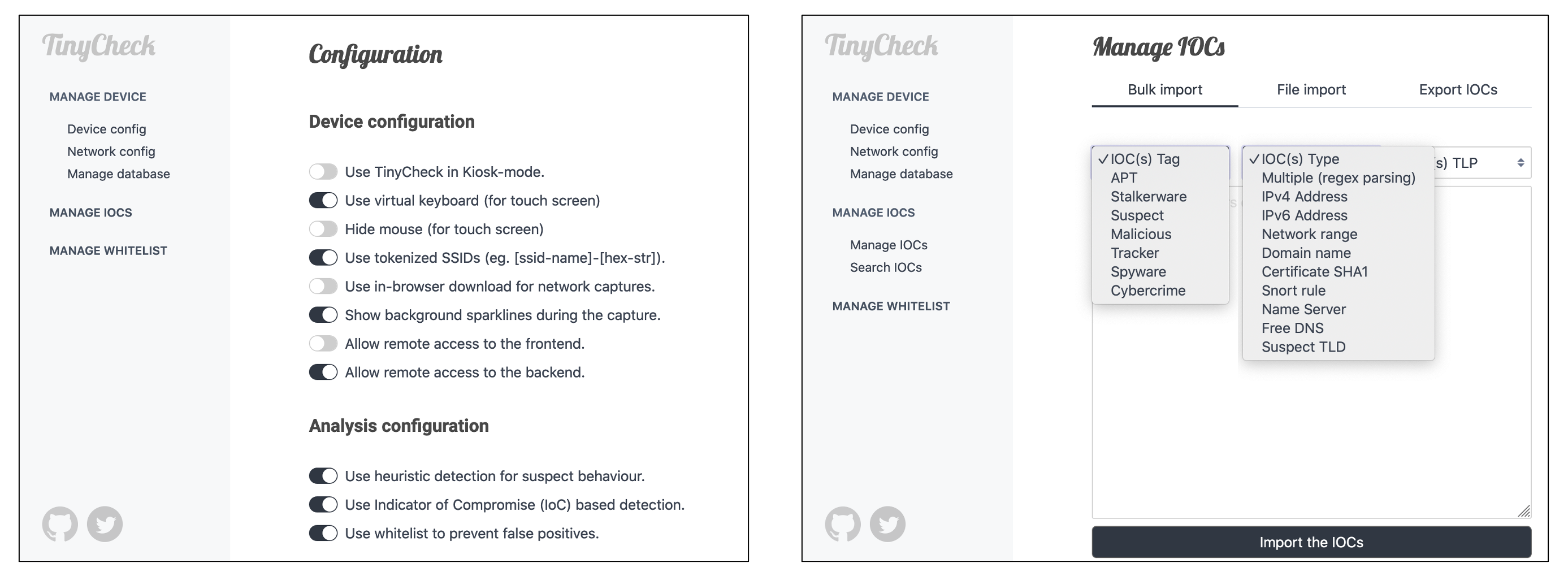
Once installed, you can connect yourself to the TinyCheck backend by browsing the URL https://tinycheck.local and accepting the SSL self-signed certificate.
The backend allows you to edit the configuration of TinyCheck, add extended IOCs and whitelisted elements in order to prevent false positives. Several IOCs are already provided such as few suricata rules, FreeDNS, Name servers, CIDRs known to host malicious servers and so on.
Questions & Answers
Your project seem very cool, does it send data to Kaspersky or any telemetry server?
No, at all. You can look to the sources, the only data sent by TinyCheck is an HTTP GET request to a website that you can specify in the config, as well as the watchers URLs. Kaspersky don't - and will not - receive any telemetry from your TinyCheck device.
Can you list some hardware which can be used with this project (touch screen, wifi dongle etc.)?
Unfortunately, we prefer to not promote any hardware/constructor/website on this page. Do not hesitate to contact us if you want specific references.
I'm not very confortable with the concept of "watchers" as the IOCs downloaded are public. Do you plan to develop a server to centralize AMBER/RED IOCs?
Yes, if the demand is felt by NGOs (contact us!). Is it possible to develop this kind of thing, allowing you to centralize your IOCs and managing your fleet of TinyCheck instances on a server that you host. The server can also embed better detection rules thanks to the telemetry that it will receive from devices.
Special thanks
Guys who provided some IOCs
- Cian Heasley for his android stalkerwares IOC repo, available here: https://github.com/diskurse/android-stalkerware
- Te-k for his stalkerwares awesome IOCs repo, available here: https://github.com/Te-k/stalkerware-indicators
- Emilien for his Stratum rules, available here: https://github.com/kwouffe/cryptonote-hunt
- Costin Raiu for his geo-tracker domains, available here: https://github.com/craiu/mobiletrackers/blob/master/list.txt
Code review
- Dan Demeter @_xdanx
- Maxime Granier
- Florian Pires @Florian_Pires
- Ivan Kwiatkowski @JusticeRage
Others
- GReAT colleagues.
- Tatyana, Kristina, Christina and Arnaud from Kaspersky (Support and IOCs)
- Zeek and Suricata awesome maintainers.
- virtual-keyboard.js.org & loading.io guys.
- Yan Zhu for his awesome Spectre CSS lib (https://picturepan2.github.io/spectre/)